7 Temmuz 2019 Pazar
11 Firefox Add-ons a Hacker Must Have
11 Firefox Add-ons a Hacker Must Have
1. Tamper Data
Tamper data is a great tool to view and modify HTTP/HTTPS headers and post parameters. We can alter each request going from our machine to the destination host with this. It helps in security testing web applications by modifying POST parameters. It can be used in performing XSS and SQL Injection attacks by modifying header data.
Add Tamper data to Firefox:
https://addons.mozilla.org/en-us/firefox/addon/tamper-data/
2. Firebug
Firebug is a nice add-on that integrates a web development tool inside the browser. With this tool, you can edit and debug HTML, CSS, and JavaScript live on any webpage to see the effect of changes. It helps while analyzing JS files to find XSS vulnerabilities. It’s a very helpful add-on for finding DOM based XSS for security testing professionals.
Add Firebug to your browser:
https://addons.mozilla.org/en-US/firefox/addon/firebug/
3. Hackbar
Hackbar is a simple penetration tool for Firefox. It helps in testing simple SQL injection and XSS holes. You cannot execute standard exploits but you can easily use it to test whether or not vulnerability exists. You can also manually submit form data with GET or POST requests. It also has encryption and encoding tools. Most of the time, this tool helps while testing XSS vulnerability with encoded XSS payloads. It also supports keyboard shortcuts to perform various tasks. I am sure most people in the security field already know about this tool. Hackbar is mostly used in finding POST XSS vulnerabilities because it can send POST data manually to any page you like. With the ability to manually send POST form data, you can easily bypass client side validations. If your payload is being encoded at client side, you can use an encoding tool to encode your payload and then perform the attack. If the application is vulnerable to XSS, I am sure you will find the vulnerability with the help of the Hackbar add-on to Firefox browser.
Add Hackbar to Firefox:
https://addons.mozilla.org/en-US/firefox/addon/hackbar/
4. Cookies Manager
Cookie Manager is one of the greatest tools ever created. Using this tool you can actually play with cookies. You can alter almost every cookie using this tool. You can use Cookies Manager to view, edit, and create new cookies. It also displays extra information about cookies, allowing you to edit multiple cookies at once and backup/restore them.
Add Cookies Manager to Firefox:
https://addons.mozilla.org/en-US/firefox/addon/cookies-manager-plus/
5. NoScript
No Script add-on is greatness beyond imagination. With this tool, you can monitor each and every script running on a website; you can block any of the scripts and see what each script actually does. But this add-on is for experts, newbies will face problems using this. Note: If you are testing XSS, HTTPS header modifications, or Injection attacks on any website, you need to disable this plugin first because it will block your efforts.
Add NoScript to Firefox:
https://addons.mozilla.org/en-us/firefox/addon/noscript/
6. Grease Monkey
Grease Monkey is the counter part to NoScript, its function is the exact opposite of Noscript. We use Noscript to block scripts and GreaseMonkey to run them. It allows you to customize the way a web page displays or behaves by using small bits of JavaScript.
Add Grease Monkey to Firefox:
https://addons.mozilla.org/en-US/firefox/addon/greasemonkey/
7. User Agent Switcher
User Agent Switcher adds a one-click user agent switch to the browser, along with a menu and tool bar button. Whenever you want to switch the user agent, use the browser button. User Agent add-on helps in spoofing the browser while performing an attack.
Add User Agent Switcher to Firefox:
https://addons.mozilla.org/en-US/firefox/addon/user-agent-switcher/
8. CryptoFox
CryptoFox is an encryption or decryption tool for Mozilla Firefox. It supports most of the available encryption algorithms so you can easily encrypt or decrypt data with supported encryption algorithms. This add-on comes with dictionary attack support to crack MD5 cracking passwords. Although it hasn’t always had great reviews, it works satisfactorily.
Add CryptoFox to Firefox:
https://addons.mozilla.org/en-US/firefox/addon/cryptofox/
9. SQL Inject Me
SQL Inject Me is another nice Firefox add-on used to find SQL injection vulnerabilities in web applications. This tool does not exploit vulnerabilities but displays their existence. SQL injection is one of the most harmful web application vulnerabilities, it can allow attackers to view, modify, edit, add, or delete records in a database. This tool sends escape strings through form fields and searches database error messages. If it finds a database error message, it marks the page as vulnerable. Hackers can use this tool for SQL injection testing.
Add SQL Inject Me to Firefox:
https://addons.mozilla.org/en-us/firefox/addon/sql-inject-me/
10. XSS ME
Cross Site Scripting is the most common web application vulnerability. This add-on is incredibly useful for detecting XSS vulnerabilities in web applications. XSS-Me is used to find reflected XSS vulnerabilities from a browser. It scans all forms of the page, and then performs an attack on selected pages with pre-defined XSS payloads. After the scan is complete, it lists all the pages that rendered a payload, and may be vulnerable to XSS attack. Then, you can manually test the web page to determine whether or not the vulnerability exists.
Add XSS ME to Firefox:
https://addons.mozilla.org/en-us/firefox/addon/xss-me/
11. Passive Recon
Last but not the least, Passive Recon is an information gathering tool.
Passive Recon provides information security professionals the ability to perform “packetless” discoveries of target resources utilizing publicly available information. It gathers information in the same manner as DnsStuff tool, available on backtrack.
Add PassiveRecon to Firefox:
https://addons.mozilla.org/en-US/firefox/addon/passiverecon/
That’s all for today. I hope you’re enjoying your journey towards becoming a Professional Hacker. Have fun! Keep learning.
29 Ocak 2019 Salı
Website Information Gathering with Red Hawk on Kali.
Welcome back hackers and pentesters to a tutorial on an all in one information gathering, and vulnerability analysis with a linux tool called Red Hawk. Recon and mapping out our target is a key step before we begin to hack or exploit anything. This tool helps automate this by seeing what our targeted site is running and if there are any exploits for it. Lets install it from our terminal and change to its directory, and then run it:
git clone github.com/Tuhinshubhra/RED_HAWK
Then change to red hawk directory:
cd RED_HAWK
Now lets run it:
php rhawk.php
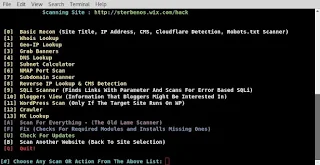
Now enter your website and hit enter. Then specify between whether it uses http or https. We now have options of what we would like red hawk to search for. we are going to go with option one. As mapping out our target site is one of the first steps in pentesting, using red hawk can easily help speed up this process by having these tools in one place.
As you can see red hawk has scanned our target site. From these we learned the target site does not use cloudflare ddos protection, runs Pepyaka version 1.13.10 ect. This is all useful information for mapping out target and from there trying to find ways we can attack. To use it agin just enter php rhawk.php from the same terminal. if you closed it change directories to RED_HAWK/ agin. Thats all for today folks, get to scanning !
29 Ekim 2017 Pazar
How To Install Oracle Java 8 In Debian Via Repository [JDK8]
Oracle Java 8 was released yesterday and it can be installed in Debian by using the WebUpd8 Java PPA repository.
Usually, the packages available in Launchpad PPAs don't support Debian because they are built against specific Ubuntu libraries, but since the WebUpd8 Oracle Java PPA contains just an installer, it works on Debian too.
Using this PPA repository, you'll be able to install Oracle Java 8 (which includes both JRE8 and JDK8) in Debian for both 32bit and 64bit as well as ARM (ARM v6/v7 Hard Float ABI - there's no JDK 8 ARM Soft Float ABI archive available for download on Oracle's website).
The installer automatically downloads and installs Oracle JDK8, but no actual Java files are available in our repository (that's not allowed by the Oracle Java license).
For Ubuntu / Linux Mint installation instructions, see: Install Oracle Java 8 In Ubuntu Via PPA Repository [JDK8]
Install Oracle Java 8 (both JDK8 and JRE8) in Debian
 |
| Tested on Debian Wheezy but it should work with any Debian version |
To add the WebUpd8 Oracle Java PPA repository and install Oracle Java 8 in Debian, use the following commands:
su -
echo "deb http://ppa.launchpad.net/webupd8team/java/ubuntu xenial main" | tee /etc/apt/sources.list.d/webupd8team-java.list
echo "deb-src http://ppa.launchpad.net/webupd8team/java/ubuntu xenial main" | tee -a /etc/apt/sources.list.d/webupd8team-java.list
apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys EEA14886
apt-get update
apt-get install oracle-java8-installer
exitAnd that's it, Oracle Java 8 should now be installed and you should get automatic updates for future Oracle Java 8 versions, under Debian.
-----------------------------------------------------------
Update October 20, 2016:
Previously, this package would increment the Java priority to make it default. The oracle-java8-installer package now sets the Java priority to 1081, and that may or may not set it as default, depending on other Java packages you may have installed (for instance, if Java 7 is also installed, Java 8 becomes default, but if Java 9 is installed, Java 8 doesn't become default).
To make Java 8 default, you must install the "oracle-java8-set-default" package (which configures the Java environment variables and sets it as default), which I added as a "Recommended" package to "oracle-java8-installer".
For instance, in Ubuntu, recommended packages are automatically installed, so "oracle-java8-set-default" should be installed when installing "oracle-java8-installer". In Linux Mint on the other hand, recommended packages are not installed by default, so you must install this package manually if you want to set Oracle Java 8 as default.
So, if you want to set Oracle Java 8 as default, no matter what other Java versions are installed, make sure that you install the oracle-java8-set-default package (which, again, should be automatically installed with the main Oracle Java Installer package in Ubuntu, but not in Linux Mint):
If you don't want to make Oracle Java 8 default (it might still be set as default, depending on what other Java versions you may have installed), install the oracle-java8-installer with "--no-install-recommends":
Note: removing the oracle-java8-set-default package does not undo all the changes (I have yet to find a way to do this properly). If you don't want to set it as default, remove both oracle-java8-installer and oracle-java8-set-default packages, and then install oracle-java8-installer with "--no-install-recommends" (like mentioned above).
Tip: if you're behind a firewall / router that blocks some of the redirects required to download the Oracle Java archive, you can download the JDK tar.gz archive manually and place it under /var/cache/oracle-jdk8-installer - then, installing the "oracle-java8-installer" package will use the local archive instead of trying it to download it itself.
After installing Oracle Java and the "oracle-java8-set-default" package, you can check out the Java version on your system by using these commands:
For how to install Oracle Java 7 in Debian, see THIS article.
For Oracle Java 9, see THIS article.
Update October 20, 2016:
Previously, this package would increment the Java priority to make it default. The oracle-java8-installer package now sets the Java priority to 1081, and that may or may not set it as default, depending on other Java packages you may have installed (for instance, if Java 7 is also installed, Java 8 becomes default, but if Java 9 is installed, Java 8 doesn't become default).
To make Java 8 default, you must install the "oracle-java8-set-default" package (which configures the Java environment variables and sets it as default), which I added as a "Recommended" package to "oracle-java8-installer".
For instance, in Ubuntu, recommended packages are automatically installed, so "oracle-java8-set-default" should be installed when installing "oracle-java8-installer". In Linux Mint on the other hand, recommended packages are not installed by default, so you must install this package manually if you want to set Oracle Java 8 as default.
So, if you want to set Oracle Java 8 as default, no matter what other Java versions are installed, make sure that you install the oracle-java8-set-default package (which, again, should be automatically installed with the main Oracle Java Installer package in Ubuntu, but not in Linux Mint):
sudo apt-get install oracle-java8-set-defaultIf you don't want to make Oracle Java 8 default (it might still be set as default, depending on what other Java versions you may have installed), install the oracle-java8-installer with "--no-install-recommends":
sudo apt-get install --no-install-recommends oracle-java8-installerNote: removing the oracle-java8-set-default package does not undo all the changes (I have yet to find a way to do this properly). If you don't want to set it as default, remove both oracle-java8-installer and oracle-java8-set-default packages, and then install oracle-java8-installer with "--no-install-recommends" (like mentioned above).
-----------------------------------------------------------
Tip: if you're behind a firewall / router that blocks some of the redirects required to download the Oracle Java archive, you can download the JDK tar.gz archive manually and place it under /var/cache/oracle-jdk8-installer - then, installing the "oracle-java8-installer" package will use the local archive instead of trying it to download it itself.
After installing Oracle Java and the "oracle-java8-set-default" package, you can check out the Java version on your system by using these commands:
java -versionjava version "1.8.0_111"
Java(TM) SE Runtime Environment (build 1.8.0_111-b14)
Java HotSpot(TM) 64-Bit Server VM (build 25.111-b14, mixed mode)javac -versionjavac 1.8.0_111For how to install Oracle Java 7 in Debian, see THIS article.
For Oracle Java 9, see THIS article.
How to accept the Oracle JDK8 license automatically
The Oracle Java 8 installer requires you to accept the Oracle license before the installation begins. If for some reason you want to accept the license automatically, you can use the following command:
echo oracle-java8-installer shared/accepted-oracle-license-v1-1 select true | sudo /usr/bin/debconf-set-selectionsUpdate: if the command above doesn't work, use the following (thanks to Adam!):
echo oracle-java8-installer shared/accepted-oracle-licence-v1-1 boolean true | sudo /usr/bin/debconf-set-selections
Install packages you want in kali linux light
Install packages you want in kali linux light
a. Always take a backup
b. Create a repo source file
c. Paste following
If you have downloaded Kali Linux 32 bit mini, Kali Linux 64 bit mini, Kali Linux 32 bit Light, Kali Linux 64 bit Light, then you might find that some tools are missing and only some basic tools are available such as nmap, Aircrack-ng.
Kali Linux provide multiple metapackages that would allow us to easily install subsets of tools based on our particular needs. After installation of kali linux mini or light version here is what you want to do first. Below is the way to install the package you want.
1. Make sure you have correct repo. for more info go to http://docs.kali.org/general-use/kali-linux-sources-list-repositories
a. Always take a backup
# mv /etc/apt/sources.list /etc/apt/sources.list_BAK
b. Create a repo source file
# vi /etc/apt/sources.list
c. Paste following
deb http://http.kali.org/kali sana main non-free contrib
deb http://security.kali.org/kali-security sana/updates main contrib non-free
deb-src http://http.kali.org/kali sana main non-free contrib
deb-src http://security.kali.org/kali-security sana/updates main contrib non-free
# sudo apt-get update
d. search available metapackages
# apt-cache search kali-linux
you can play around with apt-cache
# apt-cache -h
# apt-cache showpkg kali-linux
e. If you want kali-linux-web package then install with below command
# apt-get install kali-linux-web
Find out list of tools inside each packages: http://tools.kali.org/kali-metapackages
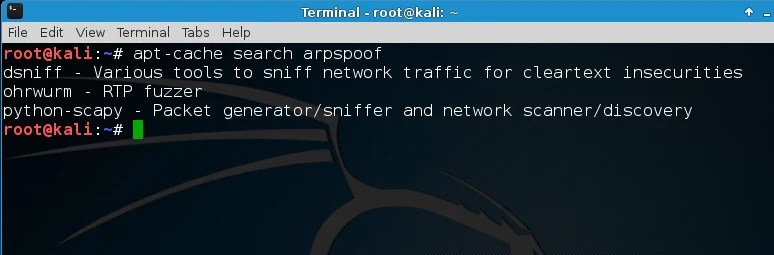
What if you just want a tool. For example, if there is no arpspoof by default and
you want to install it
# apt-cache search arpspoof
# apt-get install dsniff
There you go :)
How to Auto Install All Kali Linux Tools Using “Katoolin” on Debian/Ubuntu
Katoolin is a script that helps to install Kali Linux tools on your Linux distribution of choice. For those of us who like to use penetration testing tools provided by Kali Linux development team can effectively do that on their preferred Linux distribution by using Katoolin.
In this tutorial we are going to look at steps to install Katoolin on Debian based derivatives.
Then make /usr/bin/katoolin executable by running the command below.
Incase the above way of installation fails, you also can try the following steps.
Go to https://github.com/LionSec/katoolin.git page download the zip file and extract it.
To view contents of /etc/apt/sources.list file, select of 4.
To view the available categories, select option 2 from the main menu.
You can also install a ClassicMenu indicator using Katoolin.
To install classicmenu indicator, press
To quit Katoolin, simply press Control+C.
In this tutorial we are going to look at steps to install Katoolin on Debian based derivatives.
Major Features of Katoolin
- Adding Kali Linux repositories.
- Removing Kali Linux repositories.
- Installing Kali Linux tools.
Requirements
Requirements for installing and using Katoolin.- An operating system for this case we are using Ubuntu 14.04 64-bit.
- Python 2.7
Installing Katoolin
To install Katoolin run the following commands.# apt-get install git
# git clone https://github.com/LionSec/katoolin.git && cp katoolin/katoolin.py /usr/bin/katoolin
Sample Output
cp katoolin/katoolin.py /usr/bin/katoolin
Cloning into 'katoolin'...
remote: Counting objects: 52, done.
remote: Total 52 (delta 0), reused 0 (delta 0), pack-reused 52
Unpacking objects: 100% (52/52), done.
Checking connectivity... done.
# chmod +x /usr/bin/katoolin
Now you can run Katoolin as follows.# katoolin
The output below shows the interface of Katoolin when you run the command.Sample Output
$$\ $$\ $$\ $$\ $$\
$$ | $$ | $$ | $$ |\__|
$$ |$$ / $$$$$$\ $$$$$$\ $$$$$$\ $$$$$$\ $$ |$$\ $$$$$$$\
$$$$$ / \____$$\ \_$$ _| $$ __$$\ $$ __$$\ $$ |$$ |$$ __$$\
$$ $$< $$$$$$$ | Kali linux tools installer |$$ |$$ |$$ | $$ |
$$ |\$$\ $$ __$$ | $$ |$$\ $$ | $$ |$$ | $$ |$$ |$$ |$$ | $$ |
$$ | \$$\ \$$$$$$$ | \$$$$ |\$$$$$$ |\$$$$$$ |$$ |$$ |$$ | $$ |
\__| \__| \_______| \____/ \______/ \______/ \__|\__|\__| \__| V1.0
+ -- -- +=[ Author: LionSec | Homepage: www.lionsec.net
+ -- -- +=[ 330 Tools
1) Add Kali repositories & Update
2) View Categories
3) Install classicmenu indicator
4) Install Kali menu
5) Help
As you can see it provides a menu from which you can make selections of what you want to do.Incase the above way of installation fails, you also can try the following steps.
Go to https://github.com/LionSec/katoolin.git page download the zip file and extract it.
# wget https://github.com/LionSec/katoolin/archive/master.zip
# unzip master.zip
After extracting, you should be able to find katoolin.py script. Run katoolin.py command, you will be able to view the output similar to above.# cd katoolin-master/
# chmod 755 katoolin.py
# ./katoolin.py
How do I use Katoolin?
To add Kali Linux repositories and update repositories, select option 1 from the Menu.1) Add Kali repositories & Update
2) View Categories
3) Install classicmenu indicator
4) Install Kali menu
5) Help
kat > 1
1) Add kali linux repositories
2) Update
3) Remove all kali linux repositories
4) View the contents of sources.list file
What do you want to do ?> 1
Sample Output
Executing: gpg --ignore-time-conflict --no-options --no-default-keyring --homedir /tmp/tmp.DC9QzwECdM --no-auto-check-trustdb --trust-model always --keyring /etc/apt/trusted.gpg --primary-keyring /etc/apt/trusted.gpg --keyserver pgp.mit.edu --recv-keys ED444FF07D8D0BF6
gpg: requesting key 7D8D0BF6 from hkp server pgp.mit.edu
gpg: key 7D8D0BF6: public key "Kali Linux Repository <devel@kali.org>" imported
gpg: Total number processed: 1
gpg: imported: 1 (RSA: 1)
Then you can select option 2 from the interface above to update the repositories. From the output below, I have only captured a portion where Kali Linux repositories are being updated so that one can install Kali Linux tools in Ubuntu.What do you want to do ?> 2
Ign http://in.archive.ubuntu.com vivid InRelease
Ign http://security.ubuntu.com vivid-security InRelease
Ign http://in.archive.ubuntu.com vivid-updates InRelease
Get:1 http://security.ubuntu.com vivid-security Release.gpg [933B]
Ign http://in.archive.ubuntu.com vivid-backports InRelease
Get:2 http://repo.kali.org kali-bleeding-edge InRelease [11.9 kB]
Get:3 http://security.ubuntu.com vivid-security Release [63.5 kB]
Hit http://in.archive.ubuntu.com vivid Release.gpg
Get:4 http://repo.kali.org kali-bleeding-edge/main amd64 Packages [8,164 B]
Get:5 http://in.archive.ubuntu.com vivid-updates Release.gpg [933 B]
Get:6 http://repo.kali.org kali-bleeding-edge/main i386 Packages [8,162 B]
Hit http://in.archive.ubuntu.com vivid-backports Release.gpg
...
If you want to delete the Kali Linux repositories you added, then select option 3.What do you want to do ?> 3
All kali linux repositories have been deleted !
As part of its operation, the Apt package uses a /etc/apt/sources.list that lists the ‘sources‘ from which you can obtain and install other packages.To view contents of /etc/apt/sources.list file, select of 4.
What do you want to do ?> 4
#deb cdrom:[Ubuntu 15.04 _Vivid Vervet_ - Release amd64 (20150422)]/ vivid main restricted
# See http://help.ubuntu.com/community/UpgradeNotes for how to upgrade to
# newer versions of the distribution.
deb http://in.archive.ubuntu.com/ubuntu/ vivid main restricted
deb-src http://in.archive.ubuntu.com/ubuntu/ vivid main restricted
## Major bug fix updates produced after the final release of the
## distribution.
deb http://in.archive.ubuntu.com/ubuntu/ vivid-updates main restricted
deb-src http://in.archive.ubuntu.com/ubuntu/ vivid-updates main restricted
...
To go back you can simply type back and press [Enter] key.What do you want to do ?> back
1) Add Kali repositories & Update
2) View Categories
3) Install classicmenu indicator
4) Install Kali menu
5) Help
kat >
To go back to the main menu, simply type gohome and press [Enter] key.kat > gohome
1) Add Kali repositories & Update
2) View Categories
3) Install classicmenu indicator
4) Install Kali menu
5) Help
kat >
There are different categories of Kali Linux tools you can install on your Ubuntu using Katoolin.To view the available categories, select option 2 from the main menu.
kat > 2
**************************** All Categories *****************************
1) Information Gathering 8) Exploitation Tools
2) Vulnerability Analysis 9) Forensics Tools
3) Wireless Attacks 10) Stress Testing
4) Web Applications 11) Password Attacks
5) Sniffing & Spoofing 12) Reverse Engineering
6) Maintaining Access 13) Hardware Hacking
7) Reporting Tools 14) Extra
0) All
Select a category or press (0) to install all Kali linux tools .
You can select a category of choice or install all available Kali Linux tools by selecting option (0) and press [Enter] to install.You can also install a ClassicMenu indicator using Katoolin.
- ClassicMenu Indicator is a application indicator for the top panel of Ubuntu’s Unity desktop environment.
- ClassicMenu Indicator provides a simple way for you to get a classic GNOME-style application menu for those who prefer this over the default Unity dash menu.
To install classicmenu indicator, press
y and press [Enter].kat > back
1) Add Kali repositories & Update
2) View Categories
3) Install classicmenu indicator
4) Install Kali menu
5) Help
kat > 3
ClassicMenu Indicator is a notification area applet (application indicator) for the top panel of Ubuntu's Unity desktop environment.
It provides a simple way to get a classic GNOME-style application menu for those who prefer this over the Unity dash menu.
Like the classic GNOME menu, it includes Wine games and applications if you have those installed.
For more information , please visit : http://www.florian-diesch.de/software/classicmenu-indicator/
Do you want to install classicmenu indicator ? [y/n]> y
This PPA contains the most recent alpha/beta releases for
* Arronax http://www.florian-diesch.de/software/arronax/
* ClassicMenu Indicator http://www.florian-diesch.de/software/classicmenu-indicator/
* Privacy Indicator http://www.florian-diesch.de/software/indicator-privacy/
* RunLens http://www.florian-diesch.de/software/runlens/
* Unsettings http://www.florian-diesch.de/software/unsettings/
* UUdeLens http://www.florian-diesch.de/software/uudelens
More info: https://launchpad.net/~diesch/+archive/ubuntu/testing
Press [ENTER] to continue or ctrl-c to cancel adding it
gpg: keyring `/tmp/tmpaqk6fphl/secring.gpg' created
gpg: keyring `/tmp/tmpaqk6fphl/pubring.gpg' created
...
You can also install Kali menu in Ubuntu by select option 4 and press y and then press [Enter].To quit Katoolin, simply press Control+C.
kat > ^CShutdown requested...Goodbye...
Kaydol:
Yorumlar (Atom)